SOC Operations
SOC Operations
- Continuous Proactive Monitoring
- SIEM EDR
- Threat Response
- Recovery and Remediation
- Security Optimization
- Preventive Maintenance
SOCaaS reduces threat detection and response time by combining advanced detection, forensics, and 24x7 monitoring with SOC analysts to deliver extended protection.
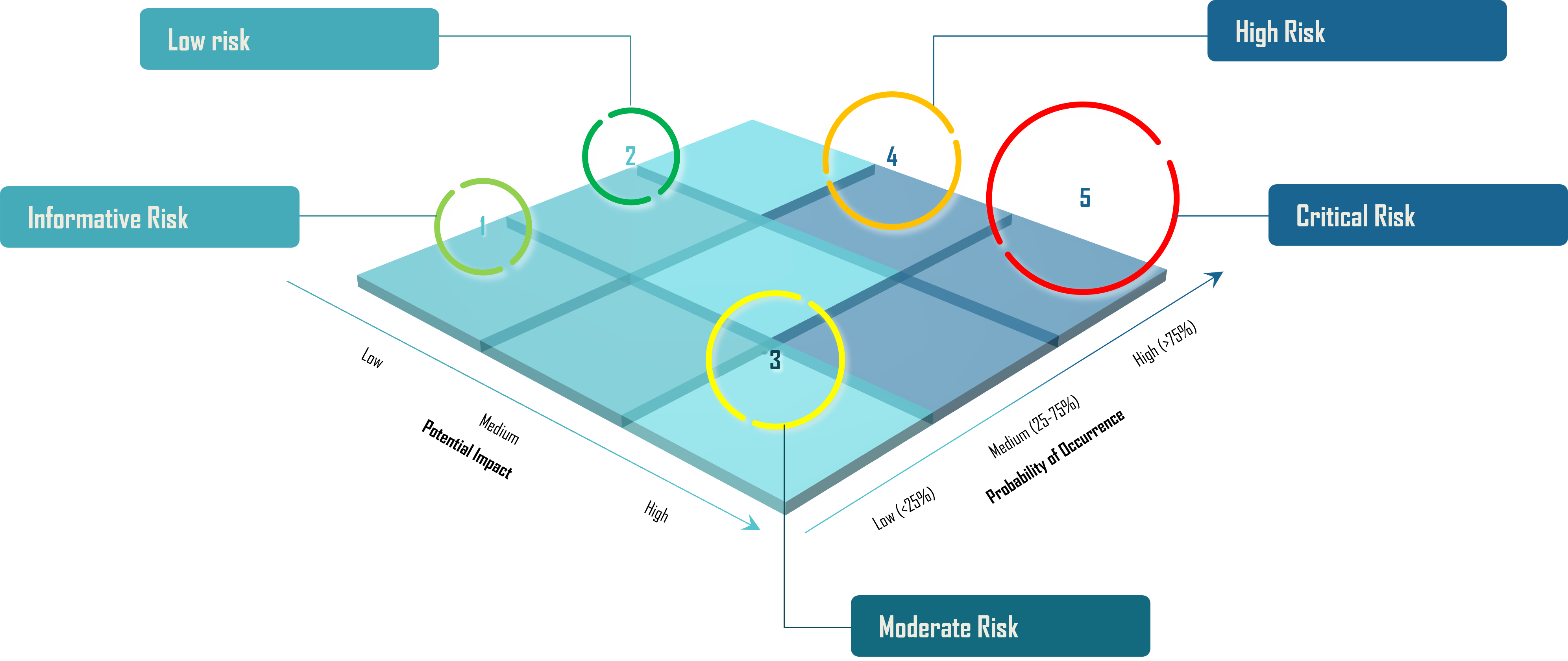
Risk Approach
Cyber Troops / CSIRTaaS
The Red Team simulates cyber attackers, using their own tools, exploiting security vulnerabilities in systems and/or applications, pivoting techniques and client objects (systems and/or applications).

Red Team
The cyber hunting troop is an active cyber defense team. It is "the process of proactively and iteratively searching across sub-networks to detect and isolate advanced threats that evade existing security solutions.

Cyber Hunter Troop
Blue Team (defensive security): is the security team that proactively defends against attacks, perform constant surveillance, analyze patterns and behaviors that are out of the ordinary in terms of security.